Category: blog
-

Celebrate Cybersecurity Awareness Month 2025: Why Employee Cybersecurity Training Matters
Every October, organizations around the world celebrate Cybersecurity Awareness Month. It’s a time to remind everyone—business owners, managers, and employees—that cybersecurity is everyone’s responsibility. In 2025, the message is clearer than ever: cyber threats are growing, and the best defense often starts with people, not technology. Many companies invest heavily in advanced firewalls, antivirus software,…
-
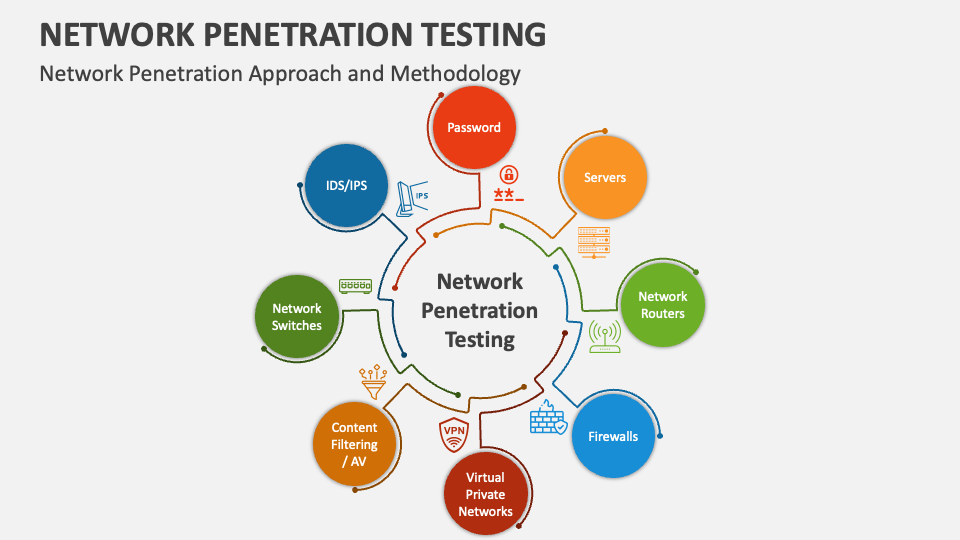
Types of Attacks That Can Be Tested in Network Penetration Testing
Network Penetration Testing (often called network pentesting) is the process of testing the security of an organization’s network infrastructure by simulating real-world attacks. The goal is to discover vulnerabilities before malicious hackers find them. In this process, an ethical hacker will attempt different attack techniques on both internal and external systems to measure how effective…
-

Why Penetration Testing Is a Must-Have Investment for Modern Cybersecurity
In today’s digital era, cyberattacks are no longer a matter of if, but when. As attack methods become more advanced, organizations across all sectors—both private and public—need to take proactive steps to identify and fix security gaps before they are exploited. One of the most effective ways to do this is through penetration testing (pentest).…
-

When Is It Time to Upgrade Your Firewall? Recognize 5 Signs Your Company Needs It!
When Is It Time to Upgrade Your Firewall? – As cyber threats grow more complex, a company’s security system must always be ready to withstand increasingly sophisticated attacks. A firewall that once protected your network effectively may now be losing its edge against the latest attack methods. If your security system begins to show weaknesses…
-
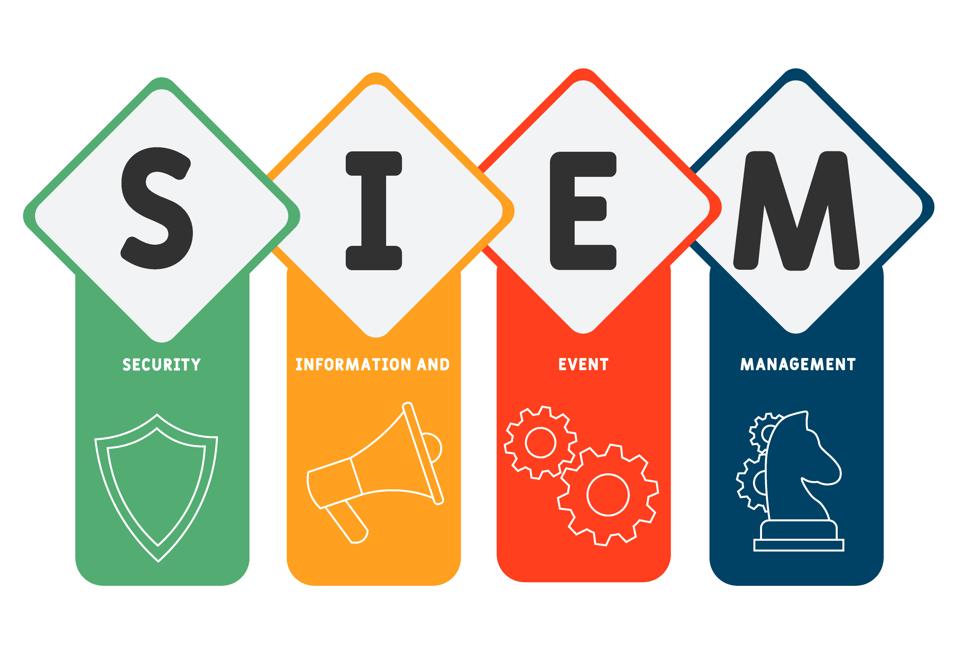
What is SIEM? An Essential Solution for Cyber Threat Detection and Response
What is SIEM? – Cybersecurity has become a top priority for companies around the world as threats grow more complex. One of the most effective solutions to address this issue is SIEM (Security Information and Event Management). With SIEM, organizations can monitor, detect, and respond to threats in real time by analyzing data from multiple…
-
Understanding Patching to Protect Systems from Cyberattacks!
Patching is the process of improving security and ensuring that a system can operate optimally by fixing bugs or vulnerabilities within it. Patching remains an essential requirement for both individuals and organizations to safeguard their systems. Typically, before patching takes place, a vulnerability assessment is performed to detect where bugs or weaknesses exist in the…
-

Data Center Security Mistakes and How to Avoid Them
Data Center Security — A data center is a core component of modern IT infrastructure, responsible for storing and managing critical data that supports smooth business operations. Despite its crucial role, data center security is often overlooked or not given enough attention. Even small mistakes—such as improper configurations or missed updates—can create vulnerabilities that cybercriminals…
-

Cybersecurity Predictions 2025: New Challenges Ahead!
Cybersecurity Predictions for 2025: New Challenges Ahead! – Cyber threats continue to evolve, bringing new challenges for individuals and organizations worldwide. In 2025, we can expect new, more complex attack patterns leveraging advanced technologies such as Artificial Intelligence (AI) and the Internet of Things (IoT). What should we do and prepare to face these threats?…
-

Are Gamers the Main Target of Malware Attacks?
Recently, an interesting report revealed that gamers remain a primary target for spreading dangerous malware. This risk arises largely because many gamers choose to download pirated games, which creates huge opportunities for cyberattacks. According to The Hacker News, hackers are using a malicious malware strain called “Winos4.0”, distributed through files often accessed by gamers. By…
-

Tips to Detect Phishing Emails You Need to Learn!
Every time you open your inbox, there’s a hidden threat waiting to strike—phishing emails. With increasingly sophisticated techniques, cybercriminals try to exploit our carelessness to steal personal information, financial data, and even identities. In this article, we’ll share important tips to help you more easily detect signs of phishing emails, recognize different types of phishing…